PCI SSF - SECURE SOFTWARE LIFECYCLE
For all payment software or software components that may be present in a payment environment and either is directly involved in storing, processing, or transmitting payment data.

- Assessor Type
- Applicability
- Validity
- Governing Body
- Data Type
- Regions
- SLC ASSESSOR
- SOFTWARE DEVELOPERS
- 3 Years
- PCI SSC
- PCI ACCOUNT DATA
- GLOBAL
NA
REQUIRED
NA
NA
Required
The Software Security Framework currently includes two standards, the Secure SLC Standard, and the Secure Software Standard.
The Secure SLC Standard defines a set of security objectives, and control objectives for software vendors to ensure the security of payment software throughout the Secure software lifecycle. The payment software is securely designed and securely developed to protect payment application sensitive data, payment transaction data, reduce application vulnerabilities, and protect against software attacks.
Applicability – The Secure SLC standard is applicable to Software vendors who develops payment software. The payment software may be directly involved in processing payments, or developed to provide service around payments.
Secure SLC Eligible Software
Payment Software category are determined based on the primary function of the application. The following are primary function of the application or component developed using the Secure SLC process. The detailed description can be found in the PCI Secure SLC program guide.
POS Suite/ General
POS Admin
POS Specialized
POS Kiosk
Payment Gateway/ Switch
Payment Back Office
Payment Middleware
POS Face to Face/ POI
Shopping Cart & Store Front
Card-Not-Present
Automated Fuel Dispenser
Payment Module
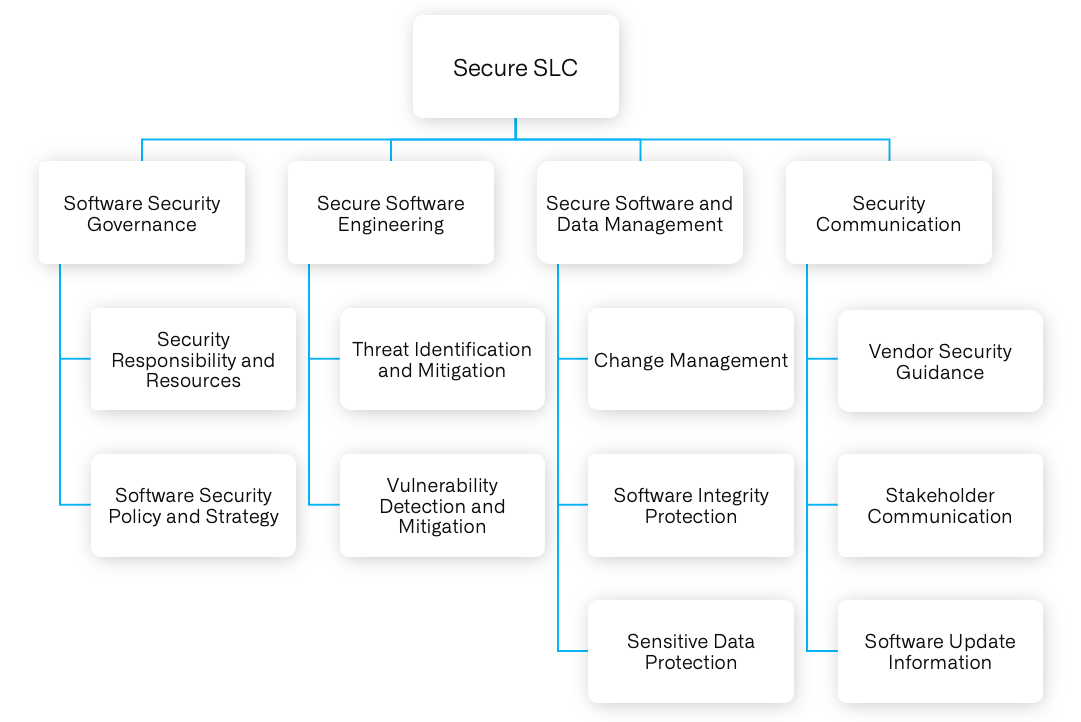
The Secure SLC Standard requirements are categorized into four major Security Objective and each Security objective defines its secure SLC Control Objective Requirements.
PCI-SSF Services
Our Secure Software Assessors have vast experience in consulting and validating wide range of payment software.
Our well trained Secure Software Assessors provides you with optimum solutions based on the current threat landscape which ensures that the application development policy, process, and software security controls that you have is validated with SSF Secure Software Standard control objective.
Our Approach
1. Scope / Application Eligibility Identification
We define the scope of Secure SLC assessment in discussion with the software vendor. The scope involves, Secure Software development lifecycle processes, Technology in use, people involved in the various stages of the development lifecycle processes. The Software vendor development business function and payment software developed were understood to determine the scope and eligibility of the software vendor for SSF Secure SLC vendor listing.
2. Pre-Requisite
The documents which will help our Secure SLC Assessor teams to get to know about the software vendor development process, Payment application developed in detail is obtained. Based on this the information, the Secure SLC Standard applicable control objective will be determined, and assessment activities are outlined.
3. Gap Assessment / Consulting
Involves identification of software SLC controls implemented with respect to the control objective given in the Secure SLC standard. Secure SLC Assessor provides consulting and the control recommendation to meet the SSF Secure SLC control objective requirements.
4. Remediation
The SSF Secure SLC Assessor teams will discuss the gap assessment report with the Software vendor stakeholders and concur on the findings and provide the relevant explanations and security control recommendation for remediation.
5. Documentation Review
The list of documents and evidence required for SSF Secure SLC Standard validation will be provided to Software vendor. The documents and evidence were collected during the assessment activities, or can be submitted to the Assessor after the assessment for Review. Review is performed to validate the policy, processes and procedure are in line with the Secure SLC Standard control objectives.
6. Final Audit
The final certification audit will be conducted once all the closures are achieved, and the Software vendor team is ready for the audit. The final audit involves verification of the controls implemented with respect to the control objective given in the Secure SLC standard.
7. Reporting
Upon completion of the final audit and achievement of Secure SLC standard control objectives, Crossbow Labs Secure SLC Assessor prepare the Reporting document ROC, and AOC document.
8. PCI Council AQM Review
The Report on Compliance (ROC) and Attestation of Compliance (AOC) will be submitted to PCI Council for their review and listing in council official website. Crossbow Labs Secure SLC Assessor will be working with PCI Council AQM Team and Software Vendor team to clarify and resubmit any queries raised by the PCI Council AQM team.
9. Qualified Vendor Listing and deliverables.
Based on successful listing of the Software Vendor in the PCI council website. The following reports will be issued to the Software vendor.
1. Attestation of Compliance (AOC)
2. Report on Compliance (ROC)
3. Certificate (COC)
Why CBL?
We help our customers with a simplified Secure SLC Assessment and Audit procedure and helps streamlining the process with the help of our innovative Compliance management solution-BOLT.
Our Automated approach in providing report, exchanging documents and workflow management saves lot efforts.
We provide customized solutions to make sure that you implement Secure SLC Controls effectively in your Payment Software developed processes.
PCI SOFTWARE SECURITY FRAMEWORK FAQs
The PCI Secure SLC Standard covers the software vendors Secure Software development lifecycle processes, Technology in use, people involved in the various stages of the development lifecycle processes.
The lifecycle stages are design, development, deployment, and maintenance of software.
The key Security objective covered as follows.
- Software Security Governance
- Secure Software Engineering
- Secure Software and Data Management
- Security Communications
The PA DSS standard is dedicated for the application within the PCI DSS environment. The PA DSS standard requirements are coupled with PCI DSS standards. However SSF Secure SLC is an independent standard not coupled with either PA DSS or PCI DSS standards. The Secure SLC is dedicated for the Software vendors Secure lifecycle development processes.
Secure SLC Qualified vendor listing changes are categories into Administrative change and Designated change.
Administrative change – changes to corporate identity changes and changes to Listing details.
Designated change – changes to the Vendor’s Listing that are limited to: Add or remove a Product Category used in Secure SLC development
