PCI SSF - software security Standard
Secure Software Standard applies to Payment Software products that is sold, distributed, or licensed to multiple organizations. Our Security professional at CBL are qualified Secure Software Assessors performs Secure Software validation testing and Consulting.


- Assessor Type
- Applicability
- Validity
- Governing Body
- Data Type
- Regions
- SSS QSA
- SOFTWARE DEVELOPERS
- 3 Years
- PCI SSC
- CARDHOLDER DATA
- GLOBAL
NA
REQUIRED
NA
NA
NA
The Secure Software Standard defines a set of security objectives, and control objectives to ensure the security of the Payment software. This is one of the standards under the PCI Software Security Framework. It covers application security features and functionality. The Secure Software Standard is also Known as S3 or SSS.
Applicability
Secure Software Standard is applicable to Payment Software products that is sold, distributed, or licensed to multiple organizations.
Secure Software Standard supports wide range of payment application that involved in or directly supporting or facilitating payment transactions that store, process, or transmit clear-text account data.
Payment Software types
POS Suite/ General
POS Admin
POS Specialized
POS Kiosk
Payment Gateway/ Switch
Payment Back Office
Payment Middleware
POS Face to Face/ POI
Shopping Cart & Store Front
Card-Not-Present
Automated Fuel Dispenser
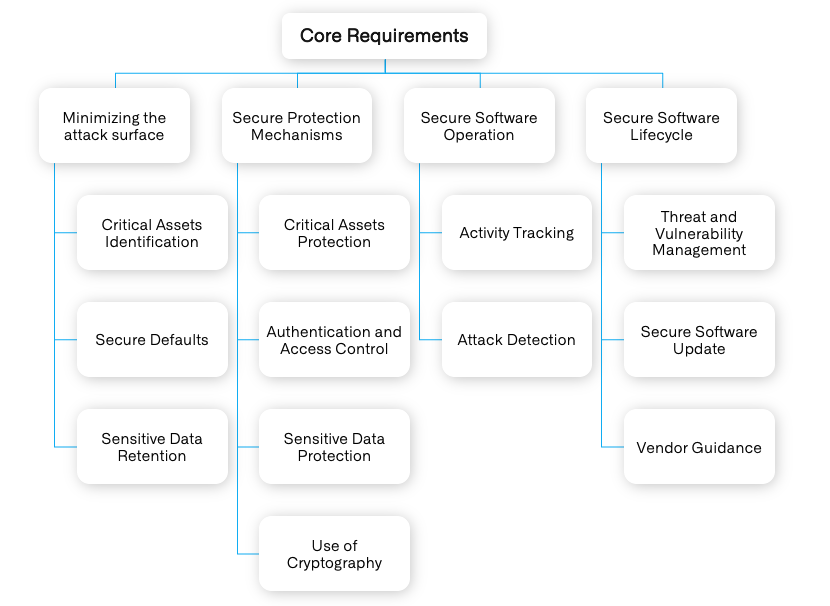
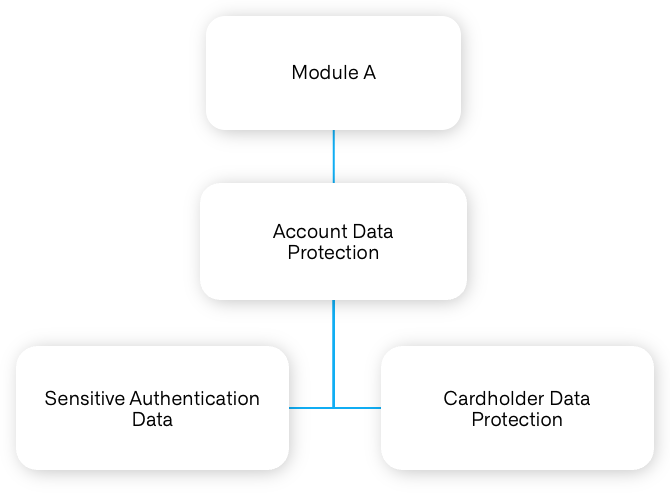
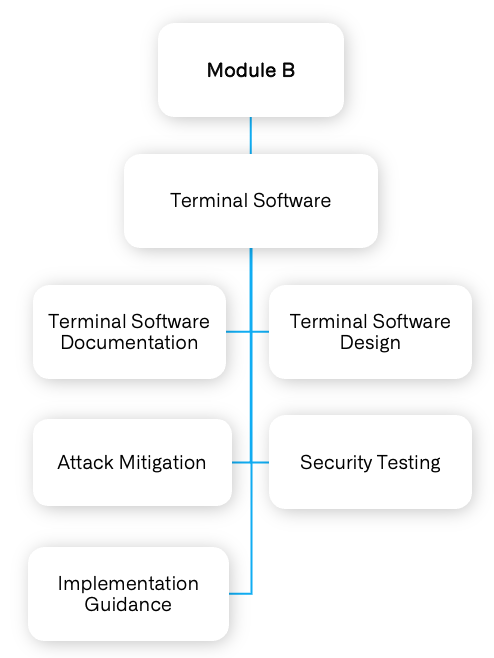
Secure Software Standard requirements are categorized into Core Requirements, Module A, and Module B.
The Core Requirements and Module A is applicable to all eligible payment software. Module B includes additional requirement for Terminal Software.
How can CBL Help?
Experience
Our Secure Software Assessors have vast experience in consulting and validating wide range of payment software.
Solutions
Based on the current threat landscape which ensures that the application development policy, process, and software security controls that you have is validated with SSF Secure Software Standard control objective.
Support
We also offer continual support to perform annual validation, and also to maintain the changes to the validated payment software ensure that your payment software latest version stays SSF Secure Software Standard validated
Our Approach
1. Scope / Application Eligibility Identification
We define the scope of Secure Software assessment in discussion with the software vendor. The application function, application modules, application dependencies, and flow of sensitive data were understood to determine the scope and eligibility of the software for SSF SSS listing.
2. Pre-Requisite
We request our customers to share the initial documents which will help our Secure Software Assessor teams to get to know about the software vendor development process, Payment application use and functionality in detail. Based on this the information, the Secure Software Standard applicable control objective will be determined, and assessment activities are outlined.
3. Gap Assessment / Consulting
Involves identification of software security controls implemented with respect to the control objective given in the Secure Software standard. Payment software testing activities will be conducted in test environment with appropriate tools and techniques. Secure Software Assessor provides the Security control recommendation to meet the SSF Secure Software control objective requirements.
4. Application Control Testing
Payment software testing activities will be conducted in test environment with appropriate tools and techniques. Software interfaces are tested to identify the current threats and vulnerabilities which may present and impact the application security and data.
5. Forensic Analysis
Cyber forensic analysis will be performed in application test environment with industry standard forensic tools and technique. Analysis is performed to identify the traces of sensitive data which may be retained by the application or by the execution environment system which were unnoticed. The forensic technique involves, disk analysis, and system memory analysis techniques.
6. Remediation
The SSF Secure Software Assessor teams will discuss the gap assessment report with the Software vendor stakeholders and concur on the findings and provide the relevant explanations and security control recommendation for remediation.
7. Documentation Review
The list of documents and evidence required for SSF Secure Software Standard validation will be provided to Software vendor. The documents and evidence were collected during the scoping and gap assessment activities, or can be submitted to the Assessor after the assessment for Review. Review is performed to validate the policy, processes and procedure are in line with the Secure Software Standard control objectives.
8. Final Audit
The final certification audit will be conducted once all the closures are achieved, and the application is ready for the audit. The final audit involves verification of software security controls implemented with respect to the control objective given in the Secure Software standard.
9. Reporting
Upon completion of the final audit and achievement of Secure software standard control objectives, Crossbow Labs Secure Software Assessor prepare the Reporting document ROV, and AOV document.
10. PCI Council AQM Review
The Report on Validation (ROV) and Attestation of Validation (AOV) will be submitted to PCI Council for their review and listing in council official website. Crossbow Labs Secure Software Assessor will be working with PCI Council AQM Team and Software Vendor team to clarify and resubmit any queries raised by the PCI Council AQM team.
11. Application Listing And Deliverables.
Based on successful listing of the payment software in the PCI council website. The following reports will be issued to the Software vendor. 1. Countersigned Attestation of Validation (AOV) 2. Report on Validation (ROV) 3. Certificate (COC)
PCI-SSF TRAINING
Crossbow Labs teams can conduct bespoke trainings on the implementation and adherence to the PCI SSF standard. Trainers have years of experience on cybersecurity advisory for securing applications and will be able to impart tremendous experiential knowledge required to quickly achieve the objectives of the PCI SSF standard.
PCI SOFTWARE SECURITY FAQs
PCI Software Security Framework (SSF) consist of two standard, Secure Software Standard (SSS), and Secure SLC Standard (Secure SLC). These are two different, and independent standard.
- Secure software standard is applicable to payment software validation. The SSS defines the software security objective for the application security feature, secure functionality, and sensitive data protection.
- Secure SLC standard is applicable to secure software development processes of payment application.
Currently mobile payment application that are designed and developed to use in consumer mobile devices are not eligible for Secure Software Standard validation. The example of eligible application and ineligible application information are given in the PCI Secure Software Standard program guide.
For both SSF Secure Software validation listing, and Secure SLC Qualified vendor listing the validity is for 3 Years.
There is annual re-validation process to check for changes in the application / listing is applicable for both Secure Software validation listing, and Secure SLC Qualified vendor listing.
Secure Software changes are categories into High impact, low impact and administrative changes.
High impact changes – Changes to the software architecture, source code, or components that handle or interact with Sensitive Data, Sensitive Functions, or Sensitive Resources will fall under High impact change category.
High Impact changes require the Payment Software to undergo a Full Software Assessment.
Low Impact changes – Changes to the software architecture, source code, or components that do not trigger High-impact Change criteria will fall under low impact changes.
Low Impact changes may be eligible for partial or Delta Assessment.
Administrative changes – changes to the Payment Software name or Vendor’s corporate entity name in the listing.
